Are you want to pass Microsoft 70-463 dumps exam in the first attempt? The Implementing a Data Warehouse with Microsoft SQL Server 2012 ( 70-463 ) exam is a 230 questions assessment in pass4itsure that is associated with the Microsoft SQL Server 2012 certification. High pass rate Microsoft 70-463 dumps exam Microsoft SQL Server 2012 questions Youtube training. "Implementing a Data Warehouse with Microsoft SQL Server 2012" is the exam name of Pass4itsure Microsoft 70-463 dumps test which designed to help candidates prepare for and pass the Microsoft 70-463 exam.
And Pass4itsure provide a wide coverage of the content of the https://www.pass4itsure.com/70-463.html exam and convenience for many of the candidates participating in the IT certification exams except the accuracy rate of 100%. It can give you 100% confidence and make you feel at ease to take the exam.
[December-2017 Microsoft 70-463 Dumps Download From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWanJic19DTmpWLUU
[December-2017 Cisco 400-251 Dumps Download From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWN3NKQ2VvYmxCMDg
Pass4itsure Latest and Most Accurate Microsoft 70-463 Dumps Exam Q&As:
Question No : 29 – (Topic 1)You are using a SQL Server Integration Services (SSIS) project that is stored in the SSIS catalog. An Environment has been defined in the SSIS catalog. You need to add the Environment to the project. Which stored procedure should you use?
A. catalog.set_environment_reference_type
B. catalog.set_environment_property
C. catalog.create_environment_reference
D. catalog.create_environment
070-463 exam Answer: C
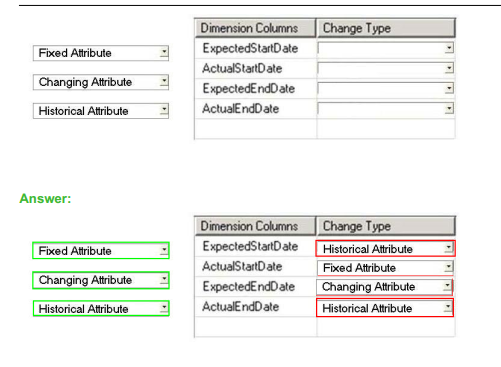
Question No : 30 DRAG DROP – (Topic 1) You are developing a SQL Server Integration Services (SSIS) package that imports data into a data warehouse. You are developing the part of the SSIS package that populates the ProjectDates dimension table. The business key of the ProjectDates table is the ProjectName column. The business user has given you the dimensional attribute behavior for each of the four columns in the ProjectDates table:
ExpectedStartDate – New values should be tracked over time.
ActualStartDate – New values should not be accepted.
ExpectedEndDate – New values should replace existing values.
ActualEndDate – New values should be tracked over time.
You use the SSIS Slowly Changing Dimension Transformation.
You must configure the Change Type value for each source column.
Which settings should you select? (To answer, select the appropriate setting or settings in the answer area. Each Change Type may be used once, more than once, or not at all.)
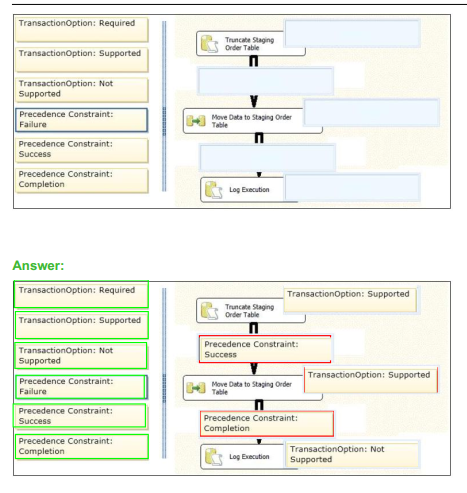
Question No : 31 DRAG DROP – (Topic 1) You are designing a SQL Server Integration Services (SSIS) package. The package moves order-related data to a staging table named Order. Every night the staging data is truncated and then all the recent orders from the online store database are inserted into the staging table. Your package must meet the following requirements: If the truncate operation fails, the package execution must stop and report an error. If the Data Flow task that moves the data to the staging table fails, the entire refresh operation must be rolled back. For auditing purposes, a log entry must be entered in a SQL log table after each execution of the Data Flow task. The TransactionOption property for the package is set to Required. You need to design the package to meet the requirements. How should you design the control flow for the package? (To answer, drag the appropriate setting from the list of settings to the correct location or locations in the answer area.)
Question No : 32 – (Topic 1)You are developing a SQL Server Integration Services (SSIS) package that imports data
into a data warehouse hosted on SQL Azure. The package uses a Foreach container to process text files found in a folder. The package must be deployed to a single server by using the Project Deployment model. Multiple SQL Server Agent jobs call the package. Each job is executed on a different schedule. Each job passes a different folder path to the package. You need to configure the package to accept the folder path from each job. Which package configuration should you use?
A. .dtsConfig file
B. Registry Entry
C. Environment Variable
D. Parent Package Variable
E. XML Configuration File
Answer: C
Reference:
You are building a SQL Server Integration Services (SSIS) package to load data from all files that are automatically copied to a directory each night through an external FTP process. You need to load data from all copied files to a destination table in SQL Server. Which three steps should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Question No : 33 DRAG DROP – (Topic 1)You are building a SQL Server Integration Services (SSIS) package to load data from all files that are automatically copied to a directory each night through an external FTP process. You need to load data from all copied files to a destination table in SQL Server. Which three steps should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)

Question No : 34 – (Topic 1)You are developing a SQL Server Integration Services (SSIS) package that imports data from a relational database to a data warehouse. You are importing data from a relational table named Projects. The table has change data capture enabled on all columns. You need to process only the most recent values from rows that have been inserted or updated since the previous execution of the package. Which query should you use as the data source?

A. Option A
B. Option B
C. Option C
D. Option D
70-463 dumps Answer: D
QUESTION NO: 35
Which of the following can be used to perform session hijacking? Each correct answer represents a complete solution. Choose all that apply.
A. Cross-site scripting
B. Session fixation
C. ARP spoofing
D. Session sidejacking
Answer: A,B,D
Explanation:
QUESTION NO: 36
Which of the following is a type of computer security vulnerability typically found in Web applications that allow code injection by malicious Web users into the Web pages viewed by other users?
A. SID filtering
B. Cookie poisoning
C. Cross-site scripting
D. Privilege Escalation
070-463 pdf Answer: C
Explanation:
QUESTION NO: 37
You want to perform passive footprinting against we-are-secure Inc. Web server. Which of the following tools will you use?
A. Nmap
B. Ethereal
C. Ettercap
D. Netcraft
Answer: D
070-463 exam Explanation:
QUESTION NO:38
Which of the following services CANNOT be performed by the nmap utility? Each correct answer represents a complete solution. Choose all that apply.
A. Passive OS fingerprinting
B. Sniffing
C. Active OS fingerprinting
D. Port scanning
Answer: A,B
Explanation:
QUESTION NO: 39
In which of the following malicious hacking steps does email tracking come under?
A. Reconnaissance
B. Gaining access
C. Maintaining Access
D. Scanning
070-463 vce Answer: A
Explanation:
QUESTION NO: 40
Which of the following rootkits is able to load the original operating system as a virtual machine, thereby enabling it to intercept all hardware calls made by the original operating system?
A. Kernel level rootkit
B. Boot loader rootkit
C. Hypervisor rootkit
D. Library rootkit
Answer: C
Explanation:
QUESTION NO: 41
John works as a Network Administrator for Net Perfect Inc. The company has a Windows-based network. The company uses Check Point SmartDefense to provide security to the network of the company. On the HTTP servers of the company, John defines a rule for dropping any kind of userdefined URLs. Which of the following types of attacks can be prevented by dropping the user defined URLs?
A. Morris worm
B. Code red worm
C. Hybrid attacks
D. PTC worms and mutations
Answer: D
Explanation:
QUESTION NO: 42
In which of the following methods does an hacker use packet sniffing to read network traffic between two parties to steal the session cookies?
A. Cross-site scripting
B. Physical accessing
C. Session fixation
D. Session sidejacking
070-463 dumps Answer: D
Explanation:
QUESTION NO: 43
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create a Web service using the .NET Framework 2.0. You call a method in the Web service. The following exception is thrown in the Web service: client.System.Web.Services.Protocols.SoapException: Server was unable to process request. System.NullReferenceException: Object reference not set to an instance of an object. You find out that it is the following line of code that throws the exception: if (Session ["StoredValue"] == null) You must ensure that the method runs without throwing any exception. What will you do to accomplish this task?
A. Modify the WebMethod attribute in the Web service so that the EnableSession property is set to true.
B. Add the following to the System.Web section of the Web.config file: <sessionState mode="InProc" />
C. Add the following to the System.Web section of the Web.config file: <httpModules> <add name="Session" type="System.Web.SessionState.SessionStateModule" /> </httpModules>
D. In the client code for the Web service's proxy object, assign a new instance of the System.Net.CookieContainer object to the CookieContainer property.
E. In the client code for the Web service's proxy object, assign a new instance of the System.Net.CookieContainer object to the EnableSession property.
Answer: A
QUESTION NO: 44
Bill works as a Software Developer for SunInfo Inc. He develops an application named SunApplication using C# .NET. The employees of the company use SunApplication for viewing and editing inventory data. SunApplication receives data from a file named MyFile.xml, which currently does not provide any information. Bill decides to write code to get information from the MyFile.xml file. Which of the following code segments will he use to resolve the issue? Each correct answer represents a complete solution. Choose all that apply.
A. FileInfo FI = new FileInfo(@"c:\temp\MyFile.xml");
Console.WriteLine("Filename " + FI.FullName );
Console.WriteLine(" Created at " + FI.CreationTime );
Console.WriteLine(" Accessed at " + FI.LastAccessTime );
B. FileInfo FI = new FileInfo ("@c:\program files\temp\MyFile.xml");
Console.WriteLine ("Filename " + FI.FullName );
Console.WriteLine(" Created at " + FI.CreationTime );
Console.WriteLine(" Accessed at " + FI.LastAccessTime );
C. FileInfo FI = new FileInfo("MyFile.xml");
Console.WriteLine("Filename " + FI.FullName );
Console.WriteLine(" Created at " + FI.CreationTime );
Console.WriteLine(" Accessed at " + FI.LastAccessTime );
D. string [email protected]"c:\windows\MyFile.xml";
FileInfo FI = new FileInfo (str);
FI.Open (FileMode.Open, FileAccess.Read);
Console.WriteLine("Filename " + FI.FullName );
Console.WriteLine(" Created at " + FI.CreationTime );
Console.WriteLine(" Accessed at " + FI.LastAccessTime );
070-463 pdf Answer: A,C,D
QUESTION NO: 45
Allen works as a Software Developer for ABC Research Center. This research center has its subsidiaries in different cities. Allen wants to retrieve a Soil Test Report for the Geological Survey Department. He wants the test report to be available to all the members of the department over the Internet. He creates an XML Web service named SampleReport. SampleReport contains a Web method named SoilTestDetails that requires additional security. Allen decides to use generic rolebased security to secure the SoilTestDetails method from unauthorized users. Allen writes code to ensure that once a user is authenticated, a user identity named Generic is created. The Generic user identity has a group membership named GeoSurvey to allow the authenticated users access to the SoilTestDetails Web method. Which of the following code segments should Allen use to accomplish the task?
A. Dim GenIdentity As GenericIdentity = New GenericIdentity("Generic", "Custom") Dim GesRoles() As String= {"GeoSurvey"} Dim GeoPrincipal As GenericPrincipal = New GenericPrincipal(GenIdentity, GeoRoles) Thread.CurrentPrincipal = GeoPrincipal
B. Dim GeoIdentity As IIdentity = New GenericIdentity("Generic", "GeoSurvey") Dim GeoPrincipal As IPrincipal = New WindowsPrincipal((WindowsIdentity) GeoIdentity) Thread.CurrentPrincipal = GeoPrincipal
C. Dim GeoIdentity As IIdentity = New GenericIdentity("Generic", "Custom") Dim WinGeoIdentity As WindowsIdentity = (WindowsIdentity) GeoIdentity Dim GeoRoles() As String = {"GeoSurvey"} Dim GenGeoPrincipal As GenericPrincipal = New GenericPrincipal(WinGeoIdentity, GeoRoles) WindowsIdentity.Impersonate(WinGeoIdentity.Token)
D. Dim MyGenericIdentity As System.Security.Principal.IIdentity = New GenericIdentity("Generic", "Custom") Dim GeoRoles() As String = {"GeoSurvey"} GenericPrincipal GenGeoPrincipal = new GenericPrincipal(MyGenericIdentity, GeoRoles); MyGenericIdentity = WindowsIdentity.GetCurrent();
070-463 exam Answer: A

Through purchasing Pass4itsure products, you can always get faster updates and more accurate Microsoft 70-463 dumps information about the examination. "Implementing a Data Warehouse with Microsoft SQL Server 2012", also known as 70-463 exam, is a Microsoft certification which covers all the knowledge points of the real Microsoft exam. Pass4itsure Microsoft 70-463 dumps exam questions answers are updated (230 Q&As) are verified by experts.
The associated certifications of 70-463 dumps is Microsoft SQL Server 2012. Pass4itsure IT expert team take advantage of their experience and knowledge to continue to enhance the quality of https://www.pass4itsure.com/70-463.html exam training materials to meet the needs of the candidates and guarantee the candidates to pass the Microsoft certification 70-483 exam dumps which is they first time to participate in.
70-463 Dumps Youtube: https://youtu.be/RE4fYFKEx7s
Posted by: colemancolemanluxenberge0272129.blogspot.com
Source: https://www.examdumpsdownload.com/high-pass-rate-microsoft-070-463-dumps-exam/